1. Introduction
Scalar instructions are transformed into vector instructions using a process known as vectorisation. As opposed to a scalar operation, which can only be performed on a pair of operands at once, this will allow the programme to do numerous operations from a single instruction. The loop is rewritten during vectorisation so that several array elements can be processed as opposed to only one array. Let’s say there are three items. A single scalar element can process the array three times, whereas vectorized instructions process all three elements at once in the same amount of time. The primary prerequisite for vectorization, “Single Instruction, Multiple Data” (SIMD), is a feature that is present on the majority of contemporary computers. An instruction set called SIMD allows for the execution of several operations. They are offered by several processors under various names, as shown in Table 1.
Table 1: Different versions of SIMD
| Processor | SIMD |
| Modern x86 chips | Streaming SIMD Extensions (SSE) instructions |
| PowerPC Chips | AltiVec instructions (Semiconductor, 2006) |
| ARM chips | NEON (arm Developer, 1995) |
When processing vast amounts of data efficiently in scientific computing, vectorization is used. Vectorized codes have the following benefits, among others: They are shorter and simpler to read, due to the modest size of the code, there are less bugs and since it is similar to mathematical equations, it is simpler to comprehend and comprehend them.
The method is improved during the process to enable the use of SIMD instructions in the processors. This increases the vector data’s capacity for calculation. This can be used to modify the data as necessary to implement SIMD operations and speed up the programme. The biggest drawback of this is how conditional coding is handled. This is due to the conditions, which can be resolved by masking, branching the execution flow.
As attackers can use flaws to access private data, SQL databases are susceptible to attacks and are open to the theft of sensitive information. The attackers can also seize the data and divulge it to people who need it. Therefore, it is important to protect the database’s confidentiality and against piracy. Through SQL databases, CryptDB offers protection from attackers with confidentiality (Popa et al., 2011). By assembling efficient SQL aware encryption algorithms, the SQL query processes are encrypted. The method can be applied to encrypt credential keys such that a password is all that is needed to decrypt a file. The database administrator won’t be able to examine the data because both the processes and the data are encrypted. The decrypted data won’t be accessible to the attacker, even if the server is attacked. Crypt DB has minimal overhead and can process several queries at once.
However, due to the paucity of studies connecting cryptography and vectorized processes, it is unclear what security measures are included in the CryptDB-based vectorised processing. We are unaware of any research that particularly makes use of CryptDB. As a result, the suggested research attempted to use qualitative exploratory research to investigate the security aspects in the vectorised processes utilising CryptDB. To determine the security aspects, this study will use both secondary resources, like a literature review and interviews. There will be interviews with about eight security engineers who work on databases and have knowledge of vectorized processes utilising CryptD.
2. Literature Review
For the purpose of successfully encrypting algorithms, Kepner et al., (2015) has used efficient Galois Field mathematical frameworks. More people are interested in utilising cryptology in sensors algorithms and databases as a result of the growth in the use of network sensor systems and network databases. The database systems now use vectorized Advanced Encrypted Standard (AES). Due to vectorization, the implementation is much smaller and requires 100 times less code than a standard AES implementation. Additionally, it is quick and has a practical layout. With appropriate database analytics and processing, the system reaches faster speeds that are comparable to real-time prototyping with OpenSSL.
Cipher-text Policy Hidden Vector Encryption (CP-HVE), a cypher text policy with fixed widths that Phuong et al.,(2014) has introduced. An HVE is a special kind of anonymous IBE that employs the attributes connected to the cypher text or secret keys as the main parameters and contains wildcards in the cypher text or secret key attributes. A composite ordered bi-linear group and a prime ordered bi-linear group were both used in the two separate designs. By separating the cipher-text from the plaintext, these two systems both provide good security. As opposed to the other HVE algorithms, this vectorized encryption can have a constant size.
By using matrix-vector relations, Libert et al.(2019) have completed group encryption using lattice assumptions. It has been demonstrated that the suggested model is secure under specific assumptions by its implementation in conventional models. The processes have been demonstrated using an unique system that uses public key encryption as a core component of the system. The focus of this solution, meanwhile, is more on general data than on vectorized processes. A qualitative investigation of the cryptography for vectorized processes is lacking, as may be shown from the studies mentioned above. Thus, by employing CryptDB, this effort will develop a methodology for identifying the issues with the research on providing security to vectorized data.
3. Motivation and Scope of the research
The proposed research examines the use of vectorized processes in databases and CryptDB’s security. Through vectorization, the Hive configuration may carry out bulk processing as opposed to individual processes. The use of the instruction pipelines and cache is improved since each batch is viewed as an array and operations are carried out on a column vector. There is very little research on this, despite the fact that it is a crucial procedure for enhancing the speed of the operations. Because there are still security risks on the servers, where data breaches are still frequent, this research was motivated by these concerns.
Without a doubt, this necessitates further investigation of the security measures employed by cryptDB to guard against server data theft and privacy violations. By examining, the research will assist in identifying the difficulties with the current procedure and, at the same time, offer ideas to make them more effective and efficient. Since the project is exploratory in nature, a qualitative research is therefore suggested to address the research’s purpose since this would enable the researcher to uncover fresh ideas and unexpected results (Jacobs et al., 1999).
4. Sample Objectives of the subject area
This project’s main goal is to comprehend security dangers and offer appropriate countermeasures. These are the objectives of this work:
- Literature Analysis on the existing research
- Identifying suitable sample population for conducting the interview
- Develop interview questions based on the literature
- Conduct interview among security engineers
- Identifying the factors, the affect the security of the vectorised processes using CryptDB.
- Cross analysis with interview and the secondary literature to identify common and new themes
- Performing the qualitative analysis to find how much these factors affect and influence the security vectorised processes using CryptDB.
- To provide recommendations for further research based on the methodological limitations arise due the challenges and constraints
5. Different research approaches used to study this area
Quantitative analysis using algorithms and coding has been carried out by numerous researchers. Along with encryption methods like CryptDB, they have modelled the vectorization process and built security algorithms. But there isn’t a method for using the responses of the security experts as part of qualitative research to pinpoint the issues. A security risk assessment evaluates the database’s risks, threats, and vulnerabilities as well as the solutions that can mitigate these risks. The specialists will utilise this analysis to identify the issues that need to be resolved. Interviews, surveys, and walkthrough observations of experts in the database and security sectors are required. In order to assure the work’s vectorization, the interviewers must look at the issues the database engineers confront.
Qualitative analysis has been used for asses the security risks in information technology by Munteanu,(2006). Quantitative and qualitative data are compared once a rigorous evaluation of the current standards has been completed. Time restraints and the analyst’s moral character have been highlighted as reasons for security threats. The preference of security engineers is for long-term security, and it is challenging to objectively estimate the cost impact of information security. Similar analysis has been performed by Albrechtsen (2007) on the performance of information security and security awareness of the engineers. In order to better understand the individual roles of information security professionals, interviews have been conducted in an IT company. It was discovered that the majority of employees had no personal security obligations; a greater workload heightens the tension between security and productivity. To improve security and performance in a way that is more evenly balanced, they must be more actively involved in the processes. A framework for network security has been created by Li et al.,(2019). Studies that are connected to this one and concentrate on network security have had their designs altered to ensure security, passive defence, strategy creation, and trend forecasting overall. Comparing the connected articles has enabled a thorough critical examination to be completed. The procedure entails the representation of the model, analysis of the solution, scenario planning, and factor gathering.
A qualitative analysis has been performed by Forde, (2017) on keeping the data secure in cloud. This qualitative study is conducted to investigate the methods used by security engineers to protect sensitive data in the cloud because the research and standards that are now available do not provide assurance of security. Responses were collected from security managers working for US federal entities. The primary variables were identified as maintaining consumer trust, avoiding out-dated encryption standards, data analysis, vulnerabilities, and training to create adequate security rules. Similar research was performed by JUNG,(2018) for South Korea using mixed methodology that comprises both quantitative and qualitative methodology. The empirical study, which focuses on the comprehensive management of cyber security, came to the conclusion that small and medium-sized companies lacked structural safeguards against security hazards. Instead, they implement the fixes after the breach occurs. As a result, they are unprepared to address any dangers and threats. External variables, risk assessment, and organisational behaviours are the three key components of the framework.
Because they engage a large number of individuals at various organisational levels, qualitative information security risk assessments are typically highly welcomed. The process can feel like it belongs to the people involved in a qualitative risk assessment. The results of qualitative risk assessments are typically less precise than those obtained with a quantitative evaluation, but they do not necessitate a lot of mathematical processing. The literature review, data collecting, and data analysis are done in order to reach the study’s scope. An successful result can be determined by looking at the relevant literature. This study, which will be unique, will examine a variety of elements.
It’s important to have a solid understanding of the descriptive and inferential parameters involved with network assaults on databases. Comparatively less time has passed since the invention of qualitative methods (Creswell, 2013). They employ descriptive techniques to comprehend the aspects under study, such as the types of assaults, difficulties encountered when integrating the vectorised algorithms with cryptography, and the incorporation of CryptDB during the vectorization process. Open ended questions are used in quantitative research, not in qualitative research. Since we must interpret the data gathered from the field, qualitative research mostly uses the inductive method. The benefits of qualitative research are as follows:
- It offers a detailed view of the subject that is investigated.
- It conveys the thoughts of the security and networking engineers.
- The background of the participants can be learnt from this.
- The views of the participants are included, not only the view of the researcher.
Its main limitation is that the data is viewed as paragraphs and cannot be visualised through graphical data.
6. Selection and justification of the preferred method
For carrying out the critical analysis, it is crucially required that the encryption used by CryptDB be complicated. The current body of research still leaves many questions unexplained. The lack of research connecting vectorization with CryptDB is a key factor in the necessity of this effort. Although CryptDB has not been utilised especially for vector codes, current research has produced encryption techniques for processes that are vectorized. A review of linked literature revealed that there has been study on the encryption of vectorized processes, particularly for qualitative data. In the section before, the value of qualitative methodology was established. To pinpoint the issues with the attacks, it is crucial to use qualitative research. We can understand the issues in the vectorized processes through the use of qualitative methodology, and by addressing the issues found through analysis, we can make these issues better.
Data collection will be carried out by locating network and security engineers who specialise in cryptography in order to analyse the information and define the key parameters through interviews. You can conduct both in-person and online interviews to make sure the data is gathered efficiently. The philosophy position that the researcher wants to adhere to heavily influences the choice of research methodology. Before identifying the factors, it is necessary to assess the research’s purpose, its own limitations, and the researcher’s personal viewpoint, as was mentioned in earlier sections. Only primary data will be gathered for the qualitative analysis in this work through conducting interviews. In this study, secondary data won’t be consulted. A more descriptive analysis will be performed using case studies.
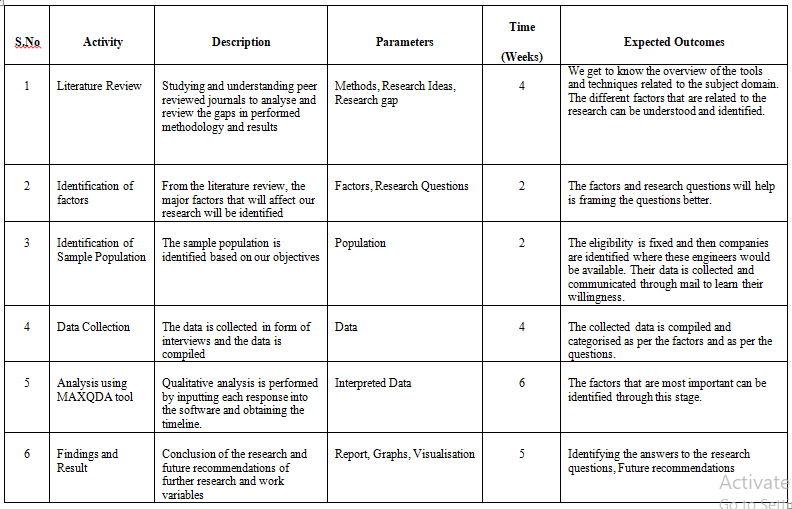
7. Test Matrix
| Input Variables | Response Variables |
| Cost | Equipment Cost Server Maintenance Cost Miscellaneous Cost |
| Time | Processing Time Execution Time Run Time
|
| Technical Person | Knowledge of the engineer Experience of the engineer Ability of the engineer |
| Cryptography | Use of Public Keys Use of Private Keys Implementation of CryptDB |
8. Research Planning
Numerous studies have explored the characteristics of research methodologies such as the goal for which it is performed, the methods chosen, and the samples. The barrier between the various designs had previously been attempted to be removed by researchers. When examining the kind of attacks in this case, figuring out the causes, and coming up with a remedy, it has been demonstrated that qualitative research is inductive in nature (Creswell, 2013). The sampling strategy for the study is determined by the representations and tactics. The choice of samples depends on the type of research study being conducted and considers both theoretical and real-world concerns. Combining probabilistic and non-probabilistic sampling has been employed by researchers. In order to learn more about the approaches, the resources that have been employed, and the proposals for the future, sampling techniques use a variety of questions. Through the use of subjective judgments in the interview, the researcher can identify respondents using the non-probabilistic sampling technique known as purposeful sampling. This will be applied in the research. Additionally, it guarantees that the respondent satisfies the prerequisites set forth by the study’s goals. The requirement in this instance is that they must be employed in the field of database security.
8.1 Brainstorming
One of the crucial phases of research is brainstorming. By reading the literature review, the study’s topic is developed. To learn more details from the relevant individuals, other sources can be consulted. Following that, the primary goals can be stated, from which a quick understanding of the research field can be drawn. The study questions and further information can be developed at this point. One can understand the benefits and drawbacks of conducting the research.
8.2 Methodology and Tools
8.2 Methodology and Tools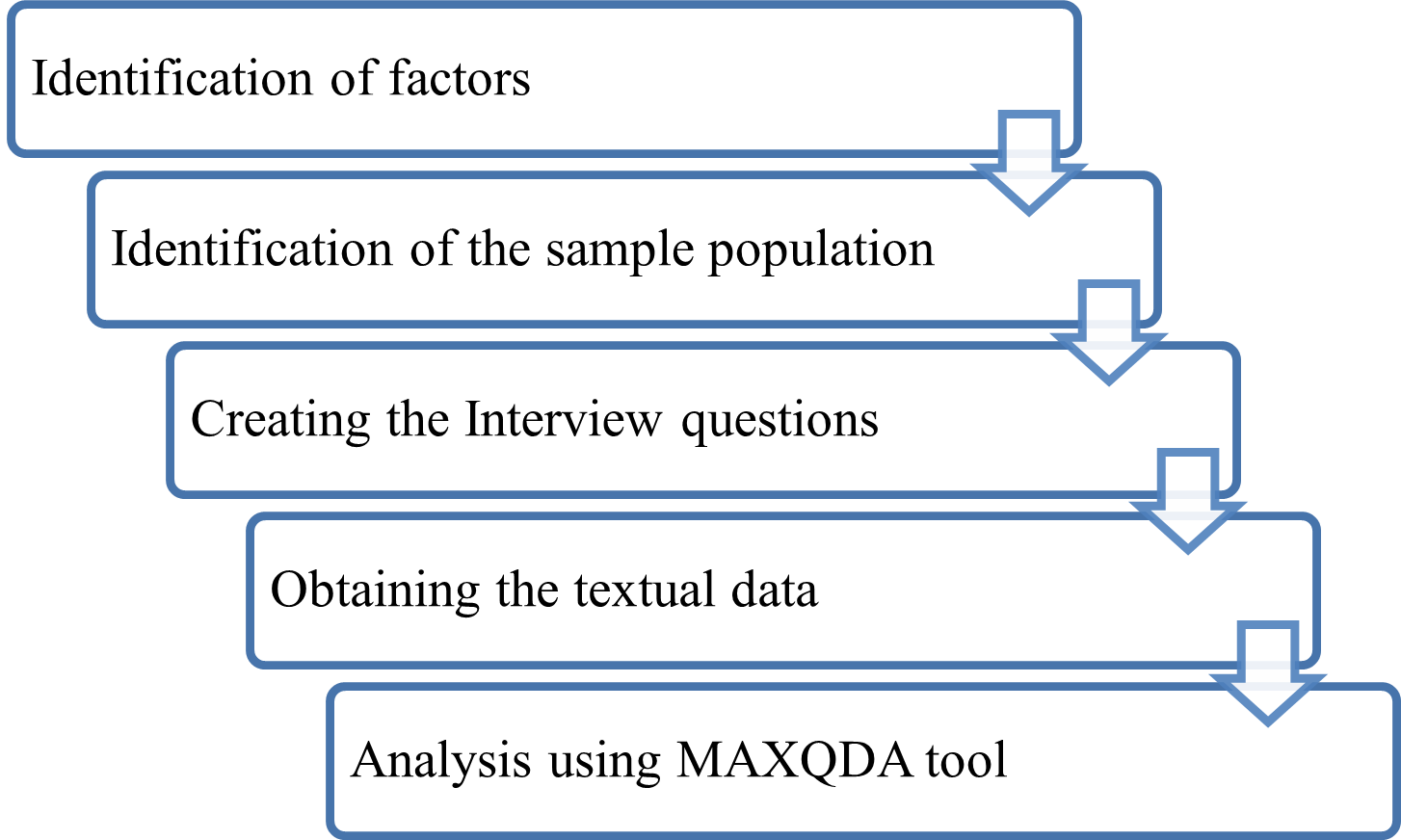
The figure illustrates the quick methodology. After developing the objectives and study questions, the first step is to identify the factors. The sample population for the interview will be chosen based on the objectives and will consist of security engineers who work with databases. The questions will be constructed based on the time and money considerations that have been made. These inquiries will either be made in person or through online forms. After that, data is gathered and assembled using the MAXQDA programme to provide an interpretation of the findings.
8.3 Sample Methods and Outcome

8.4 Resource Requirement
The respondents who were chosen to participate in the interviews will be free to answer freely and divulge as much information as they like about their job. Due to the respondents' ability to customise their responses and the fact that there is no maximum answer length, this flexibility is essential for the task. The data will be recorded and coded multiple times as part of the thematic data analysis used in this project. The computer software programmes QSR, MAXQDA, QDA Miner, and Nvivo can be used to perform the qualitative analysis. MAXQDA will be utilised in this study to analyse the data gathered.
Conclusion
A methodology for doing a qualitative analysis for enhancing the security characteristics in the vectorized processes using CryptDB has been developed as a result of this research. There isn’t much research connecting vectorized processes and cryptography, and none that uses CryptDB explicitly. Therefore, by employing CryptDB, our effort will increase the security of the vectorized processes in the database. Security engineers that work with databases will be contacted for interviews as part of the qualitative investigation. The qualitative analysis will be carried out using the MAXQDA programme.
References
Albrechtsen, E. (2007). A qualitative study of users’ view on information security. Computers & Security, 26 (4). pp. 276–289. DOI: 10.1016/j.cose.2006.11.004.
arm Developer (1995). Neon. DOI: [Accessed: 9 March 2020].
Creswell, J.W. (2013). Research design: Qualitative, quantitative, and mixed methods approaches. New York & London: Sage publications.
Forde, E.S. (2017). Security Strategies for Hosting Sensitive Information in the Commercial Cloud. Walden University,
Jacobs, J.K., Kawanaka, T. & Stigler, J.W. (1999). Integrating qualitative and quantitative approaches to the analysis of video data on classroom teaching. International Journal of Educational Research, 31 (8). pp. 717–724.
JUNG, J. (2018). A Study of Cyber Security Management within South Korean Businesses – An examination of risk and cybercrime involving industrial security. Institute of Criminal Justice Studies,
Kepner, J., Gadepally, V., Hancock, B., Michaleas, P., Michel, E. & Varia, M. (2015). Parallel vectorized algebraic AES in Matlab for rapid prototyping of encrypted sensor processing algorithms and database analytics. In: 2015 IEEE High Performance Extreme Computing Conference (HPEC). September 2015, IEEE, pp. 1–8. DOI: 10.1109/HPEC.2015.7322470.
Li, Y., Huang, G., Wang, C. & Li, Y. (2019). Analysis framework of network security situational awareness and comparison of implementation methods. EURASIP Journal on Wireless Communications and Networking, 2019 (1). pp. 205. DOI: 10.1186/s13638-019-1506-1.
Libert, B., Ling, S., Mouhartem, F., Nguyen, K. & Wang, H. (2019). Zero-knowledge arguments for matrix–vector relations and lattice-based group encryption. Theoretical Computer Science, 759. pp. 72–97. DOI: 10.1016/j.tcs.2019.01.003.
Munteanu, A. (2006). Information Security Risk Assessment: The Qualitative Versus Quantitative Dilemma. Managing Information in the Digital Economy,
Phuong, T.V.X., Yang, G. & Susilo, W. (2014). Efficient hidden vector encryption with constant-size ciphertext. In: European Symposium on Research in Computer Security. 2014, Springer, pp. 472–487.
Popa, R.A., Redfield, C.M.S., Zeldovich, N. & Balakrishnan, H. (2011). CryptDB: protecting confidentiality with encrypted query processing. In: Proceedings of the Twenty-Third ACM Symposium on Operating Systems Principles. 2011, pp. 85–100.
Semiconductor, F. (2006). AltiVec technology programming environments manual.

