Privacy And Trust Framework For Swarm Intelligence In Intrusion Detection Systems
Tagged: Computer Science
CHAPTER-II: Literature Review
Introduction
Wireless sensor networks (WSN) have steadily gained popularity across a wide range of application industries as key components of the Internet of Tings architecture. Attackers can, however, simply eavesdrop, intercept, and rebroadcast data packets because to the openness of WSN. WSN has also had numerous other security problems. WSN data security is crucially protected by intrusion detection systems (IDS). It can spot the harmful actions that try to go against network security objectives. Therefore, it is crucial to design intrusion detection methods that are efficient. But many of the IDS datasets dimensions are superfluous or redundant. Due to this, performance suffers and detection speed is slow (Xue et al., 2018).
The requirement for an extra mechanism as the final line of defense has become necessary as conventional methods fall short of effectively countering intrusion attempts. As a result, Intrusion Detection Systems (IDS) have swiftly become recognized as one of the most fundamental elements of every security system. An IDS is a security system that can spot malicious activity (already committed or ongoing) directed against a protected network or machine. Undoubtedly, creating an effective intrusion detection model is a difficult undertaking (Mahbooba et al., 2021).
Intrusion Detection System
In the modern day, using the internet, and more specifically the network, has become a staple of daily life. Organizations in both the government and non-government sectors store their crucial data in a network-wide stack. In order to manage the problems associated to secured networks, such as access control, firewall policy, and delicate data encryption, a variety of protective approaches are being deployed. Anyhow, each of these approaches has a disadvantage of its own, so relying solely on them will not result in an effective solution (Li et al., 2021).
Overview of IDS
Today's academics' top priorities have been maintaining and managing data in a secure environment while maximizing intrusion detection. There is no end to the ways that information could be accessed and altered without authorization. Such attempts look for weaknesses in the application programs as well as the operating system. Without compromising confidentiality, integrity, or authentication, intrusion detection systems are expected to spot illegal efforts. Due to susceptibility and penetration, it is not always possible to stop the intruder, hence intrusion detection with alarms is needed to prevent harm (Awotunde & Misra, 2022).
There may also be a knowledge base that contains the signatures of known attacks in some IDS types. It is necessary to regularly update this component to include the signatures of the most recent assaults because it is used by the analysis and configuration engine throughout the data analysis step. The possibility of a reaction engine exists, too (Mukherjee et al., 2020). The reaction engine may be able to function automatically or in response to a specific administrator instruction. A high-level generic IDS architecture that guards a network is shown in Fig. 1.
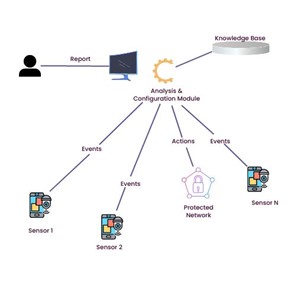
Figure 1: General architecture of a typical IDS
Different classifications of the existing IDS may be found based on various parameters. Regarding where the active sensing parts of the IDS are located, a first differentiation can be drawn. The IDS are typically divided into host-based and network-based categories based on this characteristic. In host-based techniques, every host that needs security has an IDS installed, or rather frequently only the IDS itself. A network-based IDS, on the other hand, keeps an eye on the network where the relevant hosts are located. This kind of IDS typically monitors network traffic on numerous dedicated workstations, some of which may not be the protected hosts (Awan et al., 2022).
Types of IDS
IDSs can be classified based on their design, control strategy, approaches to system monitoring, analysis strategy, and the timeliness of information sources and analysis.
IDS categories based on information sources
IDSs are typically categorized by information source, which is the most frequent method. IDSs that search for attackers examine network packets that have been recorded from LAN segments or network backbones. Other IDSs search for evidence of intrusion in data sources produced by the operating system or application software (Yang et al., 2019).
Host-based IDSThe data gathered from a specific computer system is used by host based IDSs to operate. Host-based IDSs may analyse activities with remarkable accuracy and precision from this vantage point, pinpointing precisely which users and processes are responsible for a given assault on the operating system. Host-based IDSs may directly access and monitor the data files and system activities that are typically the targets of attacks, in contrast to network-based IDSs, so they can "see" the results of an attempted attack. Operating system audit trails and system logs are often the information sources used by host based IDSs (Mohanta et al., 2020).
Network Based IDSThe network packets are captured and examined by these IDSs in order to identify assaults. One network-based IDS can monitor the network traffic affecting numerous hosts linked to the network segment by listening on the network segment or switch and defending those hosts. The sensors can be more readily protected against assault because their function is restricted to operating the IDS. To make it more challenging for an attacker to find them and determine where they are, many of these sensors are made to operate in "stealth" mode. Network-based intrusion detection systems make up the vast bulk of commercial systems (Krishna & Tyagi, 2020).
Application-Based IDSsThe events that take place inside a software application are analyzed by application-based IDSs, a unique subset of host-based IDSs. The application's transaction log files are the information sources that application based IDSs use the most frequently. Program-based IDSs are able to identify suspicious behavior brought on by authorized users beyond their authorization because they may interact directly with the application and have extensive domain or application-specific knowledge built into the analysis engine. This is since these issues are more likely to arise in user, data, and application interactions (Chang et al., 2020).
Signature-based IDSOne of the popular and reliable intrusion detection techniques is signature-based intrusion detection (misuse detection). The attack pattern is carefully examined and given a signature once a new attack has been begun. The attack code body name, the resources targeted during the assault, or the way these resources are targeted can all serve as the signature. The key drawback of this strategy is that it cannot identify new types of attacks. This method won't catch the updated copies of the old attacks if the attack pattern has been slightly changed. As a result, this method is only effective in identifying known assaults. The following method is another one for spotting new and unknown attacks (Devi.Karumanchi et al., 2019).
Anomaly-based IDSAnomaly detectors locate anomalies, or anomalous, uncommon behavior, on a host or network. They operate under the premise that assaults differ from "normal" (legal) activities and can, therefore, be detected by systems that recognize these differences. Anomaly detectors create profiles of typical user, host, or network connection behavior. These profiles are created using historical information gathered throughout a period of regular operation. The detectors then gather event data and employ several techniques to spot deviations from the usual in observed activity (Chang et al., 2020). Threshold detection, statistical measures (both parametric & non-parametric), and rule-based measures are some of the methods and approaches utilized in anomaly detection. Additionally, techniques like immune system models, genetic algorithms, and neural networks are employed. Most commercial IDSs currently in use make use of the first two precautions (Ugochukwu & Bennett, 2018).
Swarm Intelligence
The metaheuristic algorithms connected to the intelligence of swarm (SI) are stochastic in nature and inspired by the collective behaviors of either natural or artificial systems (artificial). They are based on a population of people who perform little tasks in a distributed manner and interact with one another to develop intelligent global conduct or behavior. In a strict sense, these algorithms can complete composite tasks in a relatively simple manner, which is why it is recommended to use them as a search strategy for approaches dealing with feature selection (A-Matarneh et al., 2022).
In order to control the robotic swarm in the universal optimization structure as a set of algorithms, Habib et al.(2020) popularised the concept of "Swarm Intelligence." Ant Colony Optimization (ACO), a new organically stimulated metaheuristic, was proposed by Wang & Lu, (2019) and has since been endorsed as the solution to challenging combinatorial optimization (CO) problems. The particle swarm optimization was then technologically refined by Eberhart and Kennedy, who also inspired it to replicate the gathering of flora and wildlife and their social behaviour.
The increase of shared externalities is one of swarm intelligence assemblies' key characteristics. Numerous variables affect how clever the current swarm strategies are. Some of them include the type of interactions and relationships between the agents, the brilliance of each agent, and the magnitude of a certain swarm's population. The emergence of participating swarm agents affecting development is dependent on the aspects that are acknowledged in the value that the system generates (Iwendi et al., 2021). As a result, each agent's intelligence is a crucial component and has the potential to improve the system. Such types of growth could be obtained by improving the agents' capacity for learning. Based on previous methods, this is achieved (Cai & Sharma, 2021).
The foundation of their arrangement is the main tenet for fostering SI's welfares. For instance, the net dependent parameters of SI schemes have several applications. Such circumstances could increase the swarm's capability, which ultimately improves their level of enactment. Due to the dispersion and roughness of the swarm, the layouts are highly flexible. The arrangements of swarm could be adapted to a variety of scenarios and thus be useful for a longer period depending on the degree of flexibility. For instance, in battlegrounds, this quality characteristic is beneficial (Kunhare et al., 2020).
Related work
Nandy et al.(2022) proposed a taxonomy to divide these methods into three subgroups, which include artificial cleverness, genetic and natural ideas, and computation-governed methods. However, such a categorization is too rigorous to consider all identifying strategies.
A work by Cui et al. (2021) provides a clever system that ranks features first based on the knowledge and connections/correlations learned. Then, in order to identify useful and insufficient features, feature reduction is accomplished by combining ranks obtained from acquired information as well as correlation using a novel approach. These condensed features are then provided to a feed-forward neural network for training and validation on the KDD99 dataset. Using learning techniques with quick convergence and keeping an eye out for a timely and accurate rate of discovery could also make the performance mandatory. More influential networks and research using deep neural and convolutional neural networks are required for large amounts of data.
An investigation by Li et al.(2020) designed a fuzzy entropy-centered experimental study for ant colony optimization (ACO) to investigate the world's best minimal collection of characteristics for network traffic in a real-world invasion discovering data set. Typical point-of-reference UCI datasets were used to test the proposed feature reduction approach and found it to be effective. The technique also produced favorable results when applied to the IDS dataset. The 21 features of the real-world IDS data were reduced to their top 13 features, which were then ranked using four well-known classification methods. the neural networks.
Studies Related to Machine Learning in IDS
In Ludwig (Ludwig, 2017), the author Solani & Jadav,(2020) suggested an ensemble method-based NADS based on DFN architectures, Dee Belief Network (DBN), and DNN architectures, all of which include shallow auto-encoder and DFN. The NSL-KDD dataset was used to evaluate the method, and the experiment results indicated that the method performed rather well for identifying unusual network activity. Deep learning methods have been found to significantly improve NADS performance, with high detection accuracy and low false alarm rates. To find the ideal neural weights for minimizing classification mistakes, they typically need a considerable time to process a network's data.
It is a network of interconnected nodes created to mimic the functioning of the human brain. Weights are assigned to each node's connections to various other nodes in the adjacent layer. The intrusion detection system learns to comprehend the nature of various daemons and users thanks to the neural network technique. The fundamental benefit of neural networks is their ability to handle confusing input and inaccurate output, as well as their ability to draw inferences from data without being aware of the regularities in the data up front (Mathews, 2019).
Support vector machines (SVMs) are supervised learning tasks that are connected and are used for regression and classification. It is mostly employed in anomaly detection systems and the field of pattern recognition. Instead of employing both negative and positive examples, the one class SVM is based on a single example set that belongs to a single class and positive examples. In the KDD Cup data set, it was discovered that SVM outperformed neural networks in terms of accuracy and FAR for a number of attack types (Xu et al., 2020).
Studies Related to Data Mining Techniques in IDS
Each observation with a class label is classified by a KNN process by calculating the highest confidence value among the k data points closest to the query data point. Any variation from the regular network profile is viewed as an assault by a KNN-based NADS. Because it doesn't call for parameter adaptation during the training phase, it is a strong DE for NADSs (Gerard et al., 2020). Based on the strangeness and isolation measures of its potential functions, a Dependable NIDS (DIDS) that could efficiently identify network assault was designed using the KNN approach. Overall, however, classification based IDSs strongly rely on the presumption that every classifier must be updated separately and always uses more resources than statistical methods. In the end, these strategies are incapable of identifying fresh attacks if they fail to establish usual patterns (Moustafa et al., 2019).
With the KDD CUP 99 dataset as a starting point, Selvakumar and K Muneeswaran, (B & K, 2019) suggested a new feature selection approach. We selected the appropriate features from total number of features for detecting intrusion in the network. Several feature selection methods, based on Mutual Information (MI) and wrapper with Bayesian network, C4.5 are used for feature selection. The detection performance is better with 10 features than with 41 features, and the computational cost for the classifier is lower. The right features increase the detection efficiency. Compared to the current method for feature selection, the strategy we have developed produces better results. The extended work is being done using GPU resources to speed up processing and produce better outcomes (Fitni & Ramli, 2020).
Research Gap
The network intrusion detection techniques are important to prevent our systems and networks from malicious behaviors. However, traditional network intrusion prevention such as firewalls, user authentication and data encryption have failed to completely protect networks and systems from the increasing and sophisticated attacks and malwares.
In addition, the advanced computational intelligence algorithms including genetic algorithms (GA), genetic programming (GP), artificial immune systems (AIS), and swarm intelligence (SI) are reported in Mohanraj and Santhosh (2021) as a mean for solving IDS problems. Among them, particle swarm optimization (PSO) is one of the popular SI algorithms. In several tasks, PSO has been proved to be superior when compared with GA, particularly in optimization applications (Mishra & Yadav, 2020). However, very few research work have applied PSO behavior metaphor to solve the network intrusion detection problem.
References
A-Matarneh, F.M., Alqaralleh, B.A.Y., Aldhaban, F., AlQaralleh, E.A., Kumar, A., Gupta, D. & Joshi, G.P. (2022). ''Swarm Intelligence with Adaptive Neuro-Fuzzy Inference System-Based Routing Protocol for Clustered Wireless Sensor Networks'' R. Aler (ed.), Computational Intelligence and Neuroscience, 2022. 1–11.
Awan, K.A., Din, I.U., Almogren, A. & Rodrigues, J.J.P.C. (2022). ''AutoTrust: A privacy-enhanced trust-based intrusion detection approach for internet of smart things'', Future Generation Computer Systems, 137. 288–301.
Awotunde, J.B. & Misra, S. (2022). Feature Extraction and Artificial Intelligence-Based Intrusion Detection Model for a Secure Internet of Things Networks. In: 21–44.
B, S. & K, M. (2019). ''Firefly algorithm based feature selection for network intrusion detection'', Computers & Security, 81. 148–155.
Cai, Y. & Sharma, A. (2021). ''Swarm Intelligence Optimization: An Exploration and Application of Machine Learning Technology'', Journal of Intelligent Systems, 30 (1). 460–469.
Chang, L.-H., Tsung-Han Lee, Hung-Chi Chu & Cheng-Wei Su (2020). ''Application-Based Online Traffic Classification with Deep Learning Models on SDN Networks'', Advances in Technology Innovation,
Cui, Q., Zhu, Z., Ni, W., Tao, X. & Zhang, P. (2021). ''Edge-Intelligence-Empowered, Unified Authentication and Trust Evaluation for Heterogeneous Beyond 5G Systems'', IEEE Wireless Communications, 28 (2). 78–85.
Devi.Karumanchi, P., Siva Prasad, Y, A. & Dhulipalla, N. (2019). ''Current Design Trends in Intrusion Detection System: A Review on Technologies Implemented by Researchers'', International Journal of Computer Science & Engineering Technology, 2 (4). 1109–1112.
Fitni, Q.R.S. & Ramli, K. (2020). ''Implementation of Ensemble Learning and Feature Selection for Performance Improvements in Anomaly-Based Intrusion Detection Systems''. In: 2020 IEEE International Conference on Industry 4.0, Artificial Intelligence, and Communications Technology (IAICT). July 2020, IEEE, 118–124.
Gerard, A., Latif, R., Latif, S., Iqbal, W., Saba, T. & Gerard, N. (2020). ''MAD-Malicious Activity Detection Framework in Federated Cloud Computing''. In: 2020 13th International Conference on Developments in eSystems Engineering (DeSE). 14 December 2020, IEEE, 273–278.
Habib, M., Aljarah, I. & Faris, H. (2020). ''A modified multi-objective particle swarm optimizer-based Levy flight: An approach toward intrusion detection in Internet of Things'', Arabian Journal for Science and Engineering, 45 (8). 6081–6108.
Iwendi, C., Rehman, S.U., Javed, A.R., Khan, S. & Srivastava, G. (2021). ''Sustainable Security for the Internet of Things Using Artificial Intelligence Architectures'', ACM Transactions on Internet Technology, 21 (3). 1–22.
Krishna, A.M. & Tyagi, A.K. (2020). ''Intrusion Detection in Intelligent Transportation System and its Applications using Blockchain Technology''. In: 2020 International Conference on Emerging Trends in Information Technology and Engineering (ic-ETITE). February 2020, IEEE, 1–8.
Kunhare, N., Tiwari, R. & Dhar, J. (2020). ''Particle swarm optimization and feature selection for intrusion detection system'', Sādhanā, 45 (1). 109.
Li, B., Wu, Y., Song, J., Lu, R., Li, T. & Zhao, L. (2021). ''DeepFed: Federated Deep Learning for Intrusion Detection in Industrial Cyber–Physical Systems'', IEEE Transactions on Industrial Informatics, 17 (8). 5615–5624.
Li, W., Tan, J. & Wang, Y. (2020). A Framework of Blockchain-Based Collaborative Intrusion Detection in Software Defined Networking. In: 261–276.
Ludwig, S.A. (2017). ''Intrusion detection of multiple attack classes using a deep neural net ensemble''. In: 2017 IEEE Symposium Series on Computational Intelligence (SSCI). November 2017, IEEE, 1–7.
Mahbooba, B., Timilsina, M., Sahal, R. & Serrano, M. (2021). ''Explainable Artificial Intelligence (XAI) to Enhance Trust Management in Intrusion Detection Systems Using Decision Tree Model'' A. M. Khalil (ed.), Complexity, 2021. 1–11.
Mathews, S.M. (2019). Explainable Artificial Intelligence Applications in NLP, Biomedical, and Malware Classification: A Literature Review. In: 1269–1292.
Mishra, A. & Yadav, P. (2020). ''Anomaly-based IDS to Detect Attack Using Various Artificial Intelligence & Machine Learning Algorithms: A Review''. In: 2nd International Conference on Data, Engineering and Applications (IDEA). February 2020, IEEE, 1–7.
Mohanraj, T. & Santhosh, R. (2021). ''RETRACTED ARTICLE: Security and privacy issue in multi-cloud accommodating Intrusion Detection System'', Distributed and Parallel Databases, 1.
Mohanta, B.K., Jena, D., Satapathy, U. & Patnaik, S. (2020). ''Survey on IoT security: Challenges and solution using machine learning, artificial intelligence and blockchain technology'', Internet of Things, 11. 100227.
Moustafa, N., Hu, J. & Slay, J. (2019). ''A holistic review of Network Anomaly Detection Systems: A comprehensive survey'', Journal of Network and Computer Applications, 128. 33–55.
Mukherjee, M., Matam, R., Mavromoustakis, C.X., Jiang, H., Mastorakis, G. & Guo, M. (2020). ''Intelligent Edge Computing: Security and Privacy Challenges'', IEEE Communications Magazine, 58 (9). 26–31.
Nandy, S., Adhikari, M., Khan, M.A., Menon, V.G. & Verma, S. (2022). ''An Intrusion Detection Mechanism for Secured IoMT Framework Based on Swarm-Neural Network'', IEEE Journal of Biomedical and Health Informatics, 26 (5). 1969–1976.
Solani, S. & Jadav, N.K. (2020). A Survey on Intrusion Detection System Using Artificial Intelligence. In: 67–80.
Ugochukwu, C.J. & Bennett, E.O. (2018). ''An Intrusion Detection System Using Machine Learning Algorithm'', International Journal of Computer Science and Mathematical Theory,
Wang, Q. & Lu, P. (2019). ''Research on Application of Artificial Intelligence in Computer Network Technology'', International Journal of Pattern Recognition and Artificial Intelligence, 33 (05). 1959015.
Xu, Z., Liu, W., Huang, J., Yang, C., Lu, J. & Tan, H. (2020). ''Artificial Intelligence for Securing IoT Services in Edge Computing: A Survey'', Security and Communication Networks, 2020. 1–13.
Xue, Y., Jia, W., Zhao, X. & Pang, W. (2018). ''An Evolutionary Computation Based Feature Selection Method for Intrusion Detection'', Security and Communication Networks, 2018. 1–10.

