Tips for developing intrusion detection system and significance of machine learning technique in a cloud platform
In brief (Highlights)
- You will find the best dissertation research areas / topics for future researchers enrolled in computer science engineering. These topics are researched in-depth at the University of Glasgow, UK, Sun Yat-sen University, University of St Andrews and many more
- In order to identify the future research topics, we have reviewed the computer science literature (recent peer-reviewed studies) on the security and privacy issues in the cloud environment for efficient cloud service provisioning.
- There is a possibility to minimize the security errors and develop a secure cloud model using machine learning
- Development of intrusion detection system using ML algorithm in a cloud platform is discussed.
- Download our cloud security and machine learning Reference book papers such as tutorials, proprietary materials, research projects and many more @ tutorsindia.com/academy/books
Introduction
The Machine Learning (ML) technique is used for analysing and extracting useful information from the database (Suthaharan, 2014). At present day, the adoption of ML techniques in intrusion detection system (IDS) has been looked into broadly because of its capability to give promising answers for automating detection of abnormal traffic patterns or attacks in a real-time network (Buczak & Guven, 2016), (Sommer & Paxson, 2010). Tutors India develop ML algorithms using Python, Hadoop framework and many more to booth secure access control in cloud computing platforms. Hiring our experts, you are assured with quality and on-time delivery.
In this regards, it is essential to comprehend the importance and purposes for intrusion detection results that are delivered by ML models(Sommer & Paxson, 2010). Misclassification is a typical issue in ML and a general absence of understanding into why such misclassification happens blocks the advancement and improvement of ML models. While numerous investigations concentrating on the utilization of ML in IDS have introduced improved outcomes when contrasting and different procedures, there isn’t a lot of importance on understanding the purposes behind the lower misclassification rates or improved outcomes (Lin, Ke, & Tsai, 2015; Moustafa, Slay, & Creech, 2017; Wang, Hao, Ma, & Huang, 2010). All things considered, the hidden explanations behind poor performance in the discovery of certain attack classifications are not generally clarified and can’t be seen obviously or naturally. Without a fathomable way to deal with breaking down the poor performance, the improvement of ML models more often than not depends on an experimentation procedure because of the mind-boggling nature of ML principles (Liu, Wang, Liu, & Zhu, 2017). All the more explicitly, ML models performance depends upon the qualities of testing and training datasets. Henceforth, a natural and logical investigation of such datasets can encourage the comprehension of ML recognition results(Zong, Chow, & Susilo, 2019). Hire Tutors India experts to develop your algorithm and coding implementation for your Computer Science dissertation Services.
Short note on Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) is a security tool which monitors and captures the scans the system / network, system logs and/or traffic for suspicious activities network. Furthermore, it alerts the system or cloud administrator about the network attacks (Mishra, Pilli, Varadharajan, & Tupakula, 2017). Based on the implementation of IDS system, it has been classified into four types namely, network-based IDS (NIDS), host-based IDS (HIDS), Distributed intrusion detection system (DIDS) and hypervisor-based IDS (HY-IDS)(Mishra et al., 2017; Modi et al., 2013). The pictorial representation of IDS shown in figure 1.
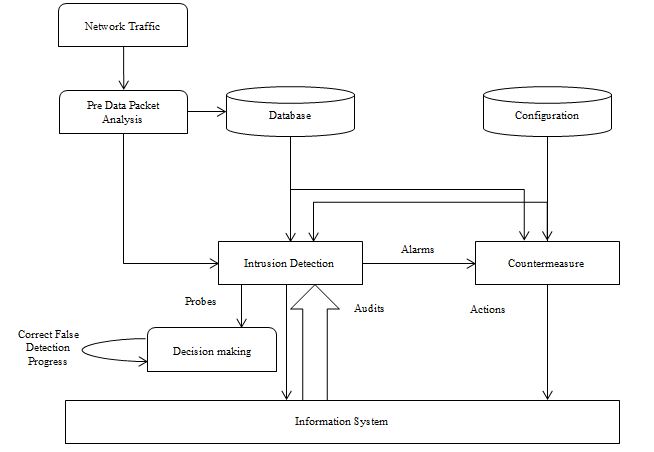
In order to detect malicious activity like port scans, DoS attacks, even attempts toward crack into computers whereas NIDS monitors network traffic. For detecting network intrusion, the collected data from network is related with the well-known attacks. Furthermore, to detect the network intruders, NIDS is a stronger detection mechanism via relating already observed behaviour with current behaviour in real-time application. In addition, NIDS detects intrusion activity and monitors the transport and IP layer headers of individual packet. It utilizes the anomaly and signature-based intrusion detection methods. But inside the host machines, the NIDS has very limited visibility. Once the network traffic data gets encoded, there is no efficient way to decode the traffic for analysis. Hire Tutors India experts to develop your algorithm and coding implementation to efficiently reduce network traffic for your Computer Science dissertation Services.
Host-based intrusion detection systems (HIDS)
The host-based IDS analyse and monitor the data which has been gathered from particular host machine. By collecting data from network events, file system and system calls, the HIDS detect intrusion of specific machine. Also, perceives changes happen in the host file system, host kernel and program behaviour. It reports the presence of network attack upon detection of deviation from expected performance/behaviour. In order to monitor the efficiency of HIDS, it depends on the selected system features.
Tutors India experts has experience in handling dissertation and assignment in computer science research with assured 2:1 distinction. Talk to Experts Now
Distributed intrusion detection system (DIDS)
A DIDS comprises the different IDS, for instance, NIDS and HIDS where it enables network monitoring or communicates with each other over a large network. Initially, intrusion detection mechanism gathers the details about system data then convert into a consistent form to be conceded to central analyser (CA). Here the term, CA is a machine which collects and analyse the data from multiple IDS. For further analysis process, the hybrid combination of signature and anomaly-based detection approach were used. The distributed IDS are used to detect both unknown and known attacks.
Hypervisor based IDS (HY-IDS)
Hypervisor is a platform to run VMs HY-IDS is running at the hypervisor layer. It permits user toward analysing and monitor the communications amongst VMs, within the hypervisor-based virtual network and hypervisor and VM based network. In addition, data availability is one of the benefits of HY-IDS.
Recommendation
From the above description, the following recommendation will give effective performance over the cloud network.
- To explore IDS based on Deep Neural Network will give better with respect to search space, intrusion detection and prevention of network traffic information.
- The simulated annealing based optimization method will be applicable to select the best set of values of parameters that involves in the building of IDS. It may avoid the error as well as manual tuning of parameters.
- To detect intrusions within encrypted packets by incorporating machine learning technique with meta-heuristic algorithms like artificial bee colony (ABC), particle swarm optimization, crow search algorithm, ant colony optimization (ACO)
- Also needs to improve the prediction performance with respect to expected intensity, type of attack or target parameters by using deep learning methods.
Tutors India develop ML algorithms using Python, Hadoop framework and many more to booth secure access control in cloud computing platforms. Hiring our experts, you are assured with quality and on-time delivery.
Summary
This section has discussed the importance of machine learning technique and detection of network traffic over the cloud environment. Also, we have recommended a solution for an effective model for both detection of known and unknown network traffic and prevention model of cloud resource over the network.
Tutors India has vast experience in developing dissertation research topics for students pursuing the UK dissertation in computer science. Order Now
References
- Buczak, A., & Guven, E. (2016). A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection. IEEE Communications Surveys & Tutorials, 18(2), 1153–1176. https://doi.org/10.1109/COMST.2015.2494502
- Lin, W.-C., Ke, S.-W., & Tsai, C.-F. (2015). CANN: An intrusion detection system based on combining cluster centers and nearest neighbors. Knowledge-Based Systems, 78, 13–21. https://doi.org/10.1016/j.knosys.2015.01.009
- Liu, S., Wang, X., Liu, M., & Zhu, J. (2017). Towards better analysis of machine learning models: A visual analytics perspective. Visual Informatics, 1(1), 48–56. https://doi.org/10.1016/j.visinf.2017.01.006
- Mishra, P., Pilli, E. S., Varadharajan, V., & Tupakula, U. (2017). Intrusion detection techniques in cloud environment: A survey. Journal of Network and Computer Applications, 77, 18–47. https://doi.org/10.1016/j.jnca.2016.10.015
- Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (2013). A survey of intrusion detection techniques in Cloud. Journal of Network and Computer Applications, 36(1), 42–57. https://doi.org/10.1016/j.jnca.2012.05.003
- Moustafa, N., Slay, J., & Creech, G. (2017). Novel Geometric Area Analysis Technique for Anomaly Detection using Trapezoidal Area Estimation on Large-Scale Networks. IEEE Transactions on Big Data, 1–1. https://doi.org/10.1109/TBDATA.2017.2715166
- Sommer, R., & Paxson, V. (2010). Outside the Closed World: On Using Machine Learning for Network Intrusion Detection. In 2010 IEEE Symposium on Security and Privacy (pp. 305–316). IEEE. https://doi.org/10.1109/SP.2010.25
- Suthaharan, S. (2014). Big data classification. ACM SIGMETRICS Performance Evaluation Review, 41(4), 70–73. https://doi.org/10.1145/2627534.2627557
- Wang, G., Hao, J., Ma, J., & Huang, L. (2010). A new approach to intrusion detection using Artificial Neural Networks and fuzzy clustering. Expert Systems with Applications, 37(9), 6225–6232. https://doi.org/10.1016/j.eswa.2010.02.102
- Zong, W., Chow, Y.-W., & Susilo, W. (2019). Interactive three-dimensional visualization of network intrusion detection data for machine learning. Future Generation Computer Systems, 102, 292–306. https://doi.org/10.1016/j.future.2019.07.045
[wce_code id=1]
